

You can never be too careful out there in the wild west that we like to call the Internet. A place where drive-by bandits can relieve you of your money, your identity, and the shirt off your back if you’re not vigilant enough.

There’s no reason why you can’t pull up the drawbridge and stop the bad guys from getting in; plenty of free (and low cost) security software tools are available. Not sure what to use? The following ten have the Mark O’Neill Seal of Approval.
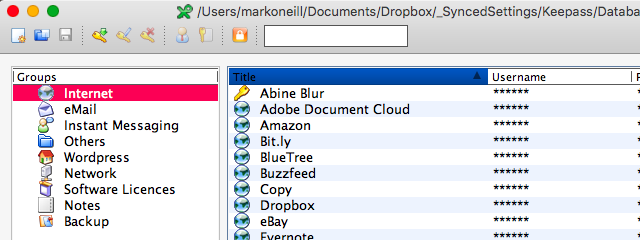
One of the most absolute drags of installing software and creating web-based accounts is having to remember yet another password. After all, we all know not to use the same password more than once – don’t we? But since @jHjddlrPoiQ#+9nB@ doesn’t exactly roll off the tongue like butter, we end up taking the easy road and instead use something really difficult like password or 123456. Then we wonder why we get hacked so easily.
The best solution to this dilemma is to use a password manager. Everyone has their favorite (LastPass, 1Password), but my favorite is KeePass, for various reasons. The password database can be left in Dropbox so it can be opened and used on every computer I am on. The iPhone version can be unlocked by Touch ID, and the required password copied to the clipboard by simply touching it. KeePass also has a password generator built in, and it tells you how strong the password is before you use it. Totally sweet.
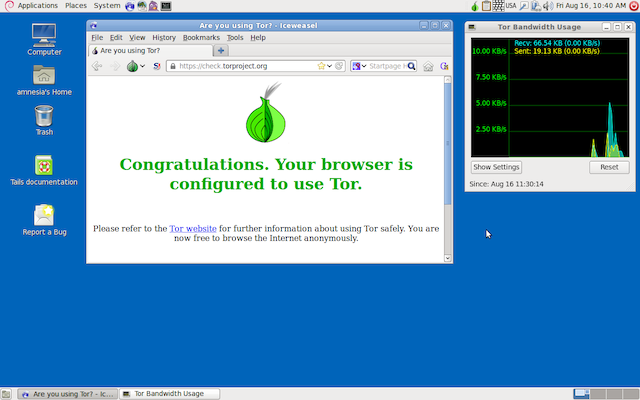
Tails (The Amnesic Incognito Live System) is a secure Linux operating system, which runs on the Tor network, and is designed to be run from a Live DVD or a Live USB stick. I am no Linux expert by any stretch of the imagination, but I found Tails very easy to set up and use.
While using it, no digital traces of what you do will be left on the computer, so this is the ideal system to test a suspicious piece of software, view some sensitive files, or carry out some private browsing, without allowing any viruses to get on to your computer.
In fact, Tails was the operating system used by Glenn Greenwald and Laura Poitras to communicate with Edward Snowden. Documents revealed by Snowden show that the NSA has serious problems breaking into the Tails system. So there’s a good reason right there why you should use Tails.
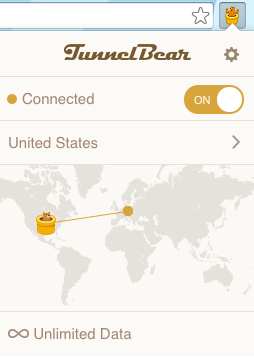
I’ve written before about my love for Tunnelbear, and it is worth mentioning again. The security advantages of a VPN are numerous, to the point where not using a VPN could be seen by some as downright reckless.
First of all, if you are using an unsecured Wi-Fi connection (say at Starbucks, or at the airport), then it is not completely safe to use. Anyone with the right equipment can snoop on your connection and scoop up sensitive information such as usernames and passwords, instant messaging chats, online banking details, and so forth. A VPN stops all that in its tracks by encrypting the data going in and out of your computer, and makes it look as if you are in another country (by assigning you a foreign IP address in the country of your choice).
What I like about Tunnelbear includes the fact that it is cheap ($5 a month for unlimited use), they provide support for numerous countries, the app is very easy to use, they have a Chrome extension which is very fast and very easy to use, their smartphone app is very well designed, and as a whole their connections are extremely stable. I have very rarely had the connection drop on me, within the past year.
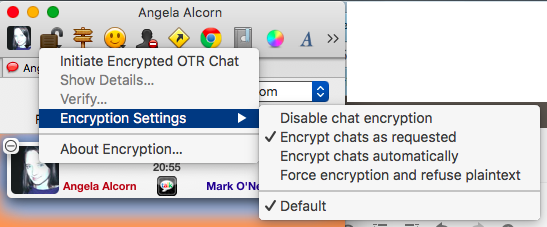
I’ve just mentioned how instant messaging can be intercepted over an unsecure Wi-Fi connection. This is why you should seriously consider using OTR (Off The Record) to encrypt your IM’s.
OTR works with Pidgin (Windows) and Adium (Mac OS X). It is a plugin which you add to Pidgin or Adium by dropping it into the plugin directory of that chat app. When you restart it, you will notice that a padlock is now in the chat window. You will have to generate private keys, but the plugin does a good job of setting all that up for you.
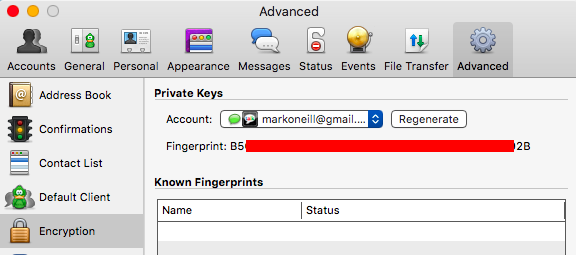
You have the choice of requesting an encrypted chat, or insisting upon it. But bear in mind that the other person in the chat must also have OTR installed for this to work. Snowden documents also reveal that the NSA has tried and failed to crack OTR.
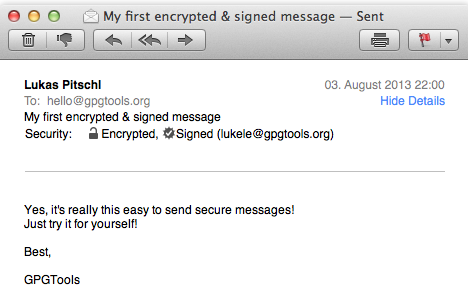
If you want to encrypt your emails, then it’s time to step up to PGP (Pretty Good Privacy).
If you use Apple Mail, Mozilla Thunderbird, or Microsoft Outlook, then you are already covered with specialized plugins (Apple Mail | Microsoft Outlook). But if desktop email is not your gig, and you are more of a webmail-based kind of dude, then there are a couple of good plugins for Gmail, notably Mymail-Crypt, and Mailvelope. Although they may be eventually made redundant by Google’s active development of an official PGP encryption plugin called End-to-End, which is currently in its alpha stage.
PGP works by generating a pair of keys – one private (also known as “secret”), and one public (here’s my public key). If you click on that link, you will see that my public key is a very long amount of meaningless gibberish. You can freely hand your public key out to everyone but you MUST keep the secret one…well, secret. If you want to send a message to someone, use their public key to encrypt and send the message, and they can then decrypt and read the message using their private key. Since the private key is private only to the owner, only the recipient can unscramble the gibberish.
If using a virtual private network seems like a bit too much for you, then at the very least use HTTPS Everywhere.
The plugin for Chrome and Firefox was developed by the Electronic Frontier Foundation (which I have written about before). HTTPS Everywhere encrypts your visits to websites, making your privacy more secure. It keeps the text of your outgoing emails private. It makes things more difficult for anyone trying to piggy-back on your Wi-Fi connection if you are having a latte in Starbucks. And when paying for something online using your credit card, HTTPS encrypts your payment details so it is not intercepted en route.
The plugin doesn’t work with every website. In that case, if the website is really important to you, you can whitelist it, so only the regular http is used. But it doesn’t conceal which sites you have visited. HTTPS Everywhere also doesn’t work with websites that don’t support the https protocol. So there are some limitations. But it’s better than nothing, and most big websites do support it.
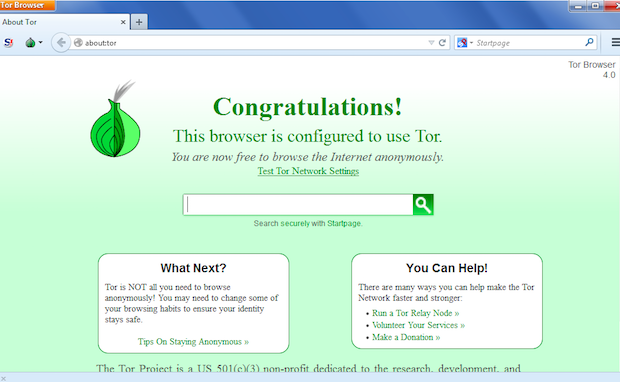
If you don’t want to install and use the Tails operating system, then at least download the Tor browser. The Tor browser is designed to keep you anonymous as you browse the web. It also enables you to visit the dark underbelly of the Internet – the so-called “Dark Web“, where drug dealers, pornographers, and hitmen ply their trade (so I’ve heard – I haven’t actually gone browsing!).
The only downside to using Tor is that it is rather slow as your Internet connection is constantly being re-routed. The upside, apart from the whole anonymity thing, is that the browser is portable. So you can run it off a USB stick, and not leave any traces on the computer you are on. It’s also cross-platform (Windows, Mac OS X, Linux).
During the whole NSA poopstorm, German chancellor Angela Merkel discovered that her phone was being tapped. So if the German chancellor of all people is not safe from people listening to her calling up the Speaking Clock, then what awaits the rest of us? That’s why you need to start encrypting your phone calls.
Signal is a free open-source app for iOS and Android which kind of mimics WhatsApp a bit. You can send instant messages with text, pictures, and video, to other Signallers who have the app and your phone number. But you can also call that person and the call will be encrypted.
I have tried it out in the past and the sound quality for calls has been extremely good. I was very impressed.
Being a huge TrueCrypt disciple, I was really upset when they announced that the project was being discontinued. What will I use now to hide all of my Katy Perry pictures? So I was somewhat mollified when I found out that another version was coming out under a different name – VeraCrypt. It’s totally identical to TrueCrypt except for a few cosmetic changes in its appearance, and a really irritating name. Vera? Really guys? That’s the best name you could come up with?
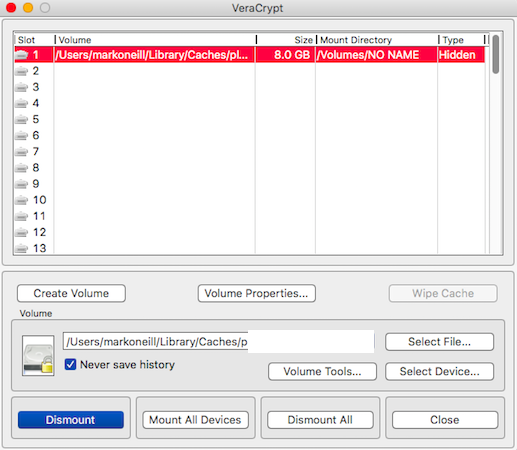
VeraCrypt (just like its predecessor) is a free software app which enables you to make encrypted folders (called “volumes”). You can also encrypt a whole hard-drive, USB stick, partition, or external hard-drive, but that is obviously a bit more advanced. You can also create a “hidden volume”, which is essentially a volume within a volume.
When you have made the volume, open it up using the interface shown above. It will then “mount” on one of your hard-drives as a folder. Just slip in what you want to hide, then unmount it again.
When TrueCrypt was around, child pornographers were using it to hide their dirty little secrets, and the FBI had serious problems cracking into the volumes. So much so that the perverts were taken to court to be ordered by a judge to hand over the password or go to jail for contempt of court. I can only assume that VeraCrypt has the same encryption strength.
One of the encryption standards you can choose when making your volume is AES, which seemingly is what the US Government uses to protect their documents up to Top Secret level. So that tells you something.

I end with a rather anti-climatic choice, but it is a solid app which has never let me down once (unlike MalwareBytes – don’t get me started on that lot). Spybot Search and Destroy (God I love that name!) is an app which searches the deepest reaches of your computer to find any nasty intruders which shouldn’t be there.
There are three versions available – the Free Edition, the Home Edition, and the Pro Edition. The last two are paid plans. The free version gives you outstanding anti-malware and anti-spyware tracking, but not in real-time. You have to manually press the button to get it going, so you have to make a point of remembering to update the app on a regular basis, and run it.
The Home edition for $13.99 gives you everything from the free version, as well as an anti-virus scanner. The Pro version for $25.99 gives you all that, and also a “Boot CD Creator” and an iPhone app scanner. Both paid plans give you real-time monitoring, multiple daily updates, and task scheduling.
And Spybot is a really good piece of software. It nuked several nasty critters from my system that MalwareBytes missed. That earned it my undying love and devotion.
What do you use to keep the baddies away? Let us know in the comments what security software apps help you sleep better at night, knowing the drawbridge is firmly up.
Image Credits:knight keeping watch by Algol via Shutterstock


 The Warring Futures Era: How the Military Shooter is Leaving the Past Behind
The Warring Futures Era: How the Military Shooter is Leaving the Past Behind Get a Free Download Manager to Speed Up Your Downloads
Get a Free Download Manager to Speed Up Your Downloads Might & Magic 3 Heroes - HD Edition (PC) review
Might & Magic 3 Heroes - HD Edition (PC) review 10+ Apps that Are Better on the iPad Pro
10+ Apps that Are Better on the iPad Pro Lego Worlds (PC) tips
Lego Worlds (PC) tips