

Industry experts have been saying for years that hackers could target critical infrastructure, including transportation, industrial control, and power systems. But with a recent attack on a Ukranian power grid, a group of Russian hackers has moved us from the realm of “could” to “can.” Here’s everything you need to know about the attack.
On December 23rd, blackouts moved across the Ivano-Frankivsk region of Ukraine, leaving around half of the region’s 1.4 million people without power. The details of the attack are still being worked out, but it appears that a group of Russian hackers launched a coordinated multi-part attack on a number of regional power distribution centers in the region.
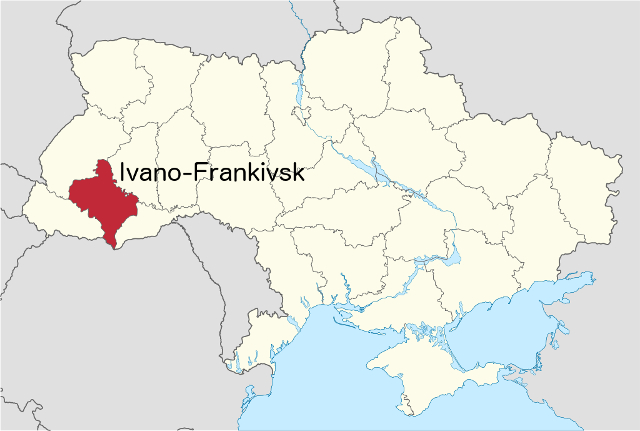
In addition to attacking the distribution centers directly, the attackers also targeted phone systems, preventing customers from reporting the power outages, and used measures to make it more difficult for technicians to discover the outage.
According to ESET, the hackers used a piece of malware called BlackEnergy to infect computers in the power grid, and another tool called KillDisk to disable them. KillDisk is very destructive: it can wipe parts of an infected hard drive, overwrite them, and make it significantly harder to restore the data. This version of KillDisk was also customized to specifically target industrial systems.

Also included in the attack was a secure SSH backdoor, allowing the hackers full access to infected systems. Whether the malware itself was responsible for the shutdown of the grid or hackers used this backdoor to access the controls isn’t immediately clear. This could potentially be an important distinction, as the malware used in the attack could be the cause of the shutdown or simply the enabler.
BlackEnergy has been used in a number of attacks against Ukrainian targets over the past year, including an attack on Ukrainian media companies in the run-up to the Ukrainian election. Russia and Ukraine have been engaged in an ongoing cyber war, with both sides launching numerous attacks, from cyber espionage and monitoring CCTV cameras to DDoS attacks and freezing funds in PayPal accounts.
ESET reports that the malware was delivered through infected macros in Microsoft Office documents, a method that’s regaining some popularity. Employees of the power companies were sent emails that appeared to come from the Ukrainian parliament – a practice called spear-phishing – and the documents attached to those emails encouraged users to run the macros, thereby infecting their computers.

The malware used in the attack was found in several power companies’ computers earlier in the year, indicating that this hack was likely planned far in advance, an idea corroborated by the complexity of the attack across multiple systems. It’s possible that the original intention was to blackout the entire country.
The attack is reminiscent of one that was used against NATO and Ukrainian officials in 2014; this one took advantage of a zero-day exploit in Microsoft Windows. The group used this exploit to spy on NATO and Ukrainian officials, and the discovery of the hack was the first time Sandworm made the news.
Sandworm is the name of the hacking group widely thought to be behind this attack. The BlackEnergy malware is strongly linked to this group, which hides references to Frank Herbert’s classic science fiction novel Dune in their code (Sandworm is a reference to a creature in the novel, seen below on the cover of Heretics of Dune).

Because their targets have largely been opponents of Russia, there’s been some speculation over whether they might have the backing of the Russian government, which makes these attacks an even more serious matter. Of course, assigning blame for these attacks is very complicated; at the moment, we’re not totally sure that Sandworm is behind the attacks, much less the Kremlin.
However, the potential ties to the Russian government make this a worrying issue. This is likely the first successful attack on a power grid, meaning that Russia is pushing their cyberwarfare capabilities forward. The US and Israel have shown similar abilities with the Stuxnet worm that destroyed nuclear centrifuges in Iran, but specifically targeting a power grid with this complex, multi-phase attack is a different story.
The US and Russia’s historically rocky relationship has a lot of people wondering if the US is prepared for this type of attack, and general answer of “no” is worrying. Of course, with some of the top cybersecurity experts in the world working for the NSA, we have some of the best defenses out there, but the fact remains that this is an unprecedented attack.
In addition to Russia’s obvious mastery of cyberwarfare, the fact that much of our critical infrastructure is outdated, especially when it comes to cybersecurity, is also very concerning. In 2014, Daniel Ross, CEO of security software company Promisec, told Forbes that critical infrastructure systems are at risk because “most of them run very old or potentially unpatched version of Windows, due to the fact that they are not taken down very often.”

The US Government Accountability Office has also made similar statements, with cyber critical infrastructure and federal information systems making its “high-risk” list in 2015. In short, yes, the US is probably at risk.
Without a devastating cyber attack, it seems unlikely that legislators will be willing to dedicate the huge amount of money it will take to properly defend US critical infrastructure and federal information systems from large-scale attacks like the one perpetrated in Ukraine. We can only hope that this event serves as an example to those in charge of cyber defense and catalyzes them to take stronger action on critical infrastructure security.
Cyberwarfare is advancing rapidly, and the ability to specifically target pieces of critical infrastructure with a multi-phase, highly planned attack has now been clearly demonstrated. We don’t know for sure if Russia was behind it, but it looks like a Russian hacking gang, possibly with the support of the Russian government, was the originator of the attack. And the US is not prepared to defend against such an attack.
What comes after power grids? Attacks on specific buildings or facilities? Military bases, maybe? Hospitals? Defense contractors? Unfortunately, the possibilities seem almost limitless, and all we can do is wait and see. How Russia, Ukraine, and the US move forward may very well have significant effects for worldwide cyberwarfare.
Does this attack on Ukraine’s power grid make you nervous? Do you feel that your country is sufficiently worried about cyber security? Or do you think this will be a wake-up call around the world? Share your thoughts below!
Image credits: TUBS via Wikimedia Commons (edited), Menna via Shutterstock.com, Kodda via Shutterstock.com, .


 Destiny: TTK - How to Level Up and Increase Light Fast
Destiny: TTK - How to Level Up and Increase Light Fast How to Upgrade Middle-Earth Shadow Of Mordor The Mithril Blade, The Wraith, The Darkness Within and more Daggers Weapon Upgrade Guide
How to Upgrade Middle-Earth Shadow Of Mordor The Mithril Blade, The Wraith, The Darkness Within and more Daggers Weapon Upgrade Guide How to Fix Resident Evil Revelations 2 Launch issues, Random Crashes, Download, Missing dll Errors, Freezing issues and more
How to Fix Resident Evil Revelations 2 Launch issues, Random Crashes, Download, Missing dll Errors, Freezing issues and more How to fix The Game of Thrones PC Launch Issues, Problems with Mac, Controller Issues, QTE Issue and more
How to fix The Game of Thrones PC Launch Issues, Problems with Mac, Controller Issues, QTE Issue and more How to fix Xbox One Black Screen of Death (BSOD)
How to fix Xbox One Black Screen of Death (BSOD)