

Oh dear. Dell is in a bit of hot water. The world’s third largest computer manufacturer has been caught shipping rogue root certificates on all of their computers, and in the process presenting a humongous security risk to all of their customers.
If that sounds strangely familiar, it’s because it is. Last year, Lenovo was caught doing virtually the same thing with its SuperFish malware, in a move that caused consumer fury, and resulted in the Chinese manufacturer being censured by the US Department of Homeland Security.
So, what’s happening? And should you be concerned?
Regardless who manufactured your computer, it came shipped with a collection of secure and trusted certificates for a few trusted servers operated by companies like Verisign and Thawte. Think of these as being like passwords, or signatures.
These certificates are essential for encryption to work. They allow you securely access encrypted web pages, download system updates, and to check the certificates of other webpages. As a result, it’s important that these certificates are handled properly.
Early on Monday morning, a Reddit user by the name of RotorCowboy (real name Kevin Hicks) submitted a text post to the Technology subreddit, warning of a self-signed root Certificate Authority (CA) that he found installed on his brand-new Dell XPS laptop, called eDellRoot.
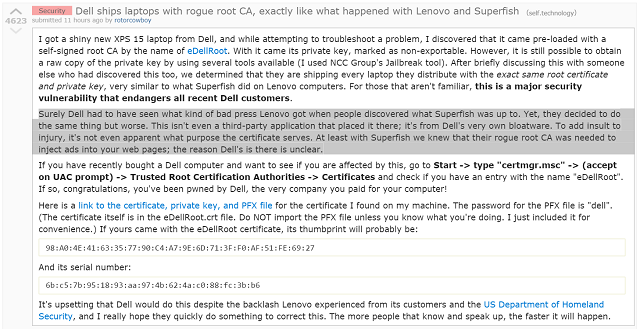
The certificate shipped with a private key, which was marked as “non-exportable”. But by using a tool produced by the NCC Group called Jailbreak, he was able to extract it. After some investigation, Hicks discovered that eDellRoot was shipping on every brand new Dell laptop with the exact same certificate and private key.
This presents a significant security risk for users. But why?
There’s a reason why e-commerce sites, online banking apps, and social networks all encrypt their traffic. Without it, anybody could intercept the messages sent from their servers to their users, and in turn get access to their private information, and even login credentials.
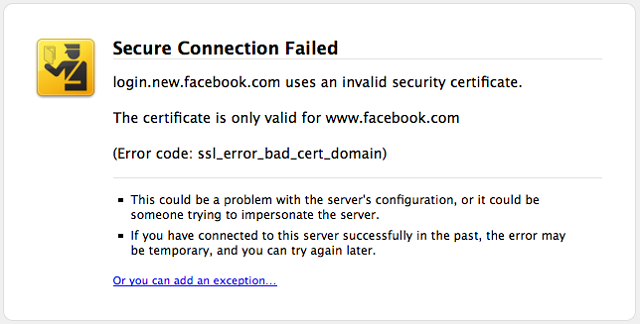
If you can preload a fake, or duplicate certificate, it then becomes possible to intercept all secure communications sent by that user, with the user being none the wiser. This type of attack is called a “man in the middle” attack.
If someone was to copy the root certificate from the Dell laptop and pretend to be the website of HSBC Bank, the user would still see the green padlock in the address bar, and would be able to interact with the site as they normally would. There would be no red screen. No warning.
But here’s where it gets really interesting. Dell shipped the same certificate and key with every Dell laptop. If you’ve bought a Dell laptop over the past year, chances are high you’re at risk.
Another terrifying side-effect of this is that it also means that an attacker would be able to sign malware with a legitimate root certificate, which would make it seem slightly more legitimate, and even obfuscate the origins of the software.
It’s nasty stuff. At this point, you could be forgiven for scratching your head, and wondering why Dell would choose to do such a thing, especially after the fallout following SuperFish.
We all know why Lenovo wanted to ship their own root CA with their computers. It allowed them to inject adverts into every single webpage. Even the encrypted ones.
Computers – particularly those at the cheaper end – are a low-margin business. Retailers don’t make much money from them, which is why you are constantly being upsold additional services and products whenever you buy a new machine. But manufacturers don’t make much money from them, either. They try to make up for that by routinely installing mountains of trialware and crapware on all new machines.
But many of the computers that’ve been identified as being infected with eDellRoot are not low end machines. The cheapest Dell XPS, for example, costs $799.
Nobody really knows what Dell’s motivations were. There’s nothing to suggest they were trying to inject their own adverts, or hijack web traffic.
So far, everything points to there being a significant lapse of judgement at Dell. Especially given that the eDellRoot CA was created six months after the SuperFish fiasco.
Note: Dell created their #eDellRoot certificate six months after Lenovo's Superfish scandal hit the news. No lessons learned.
— Mikko Hypponen (@mikko) November 23, 2015
Getting rid of eDellRoot is simple. First, open the Start menu, and search for “certmgr.msc“. This is the standard Windows tool used to manage, modify, delete and request certificates. To use it, you must be logged into an account with administrator privileges.
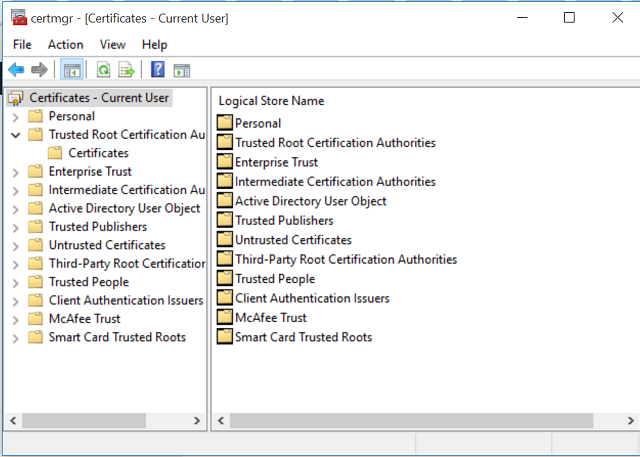
Then click on Trusted Root Certificate Authorities > Certificates. This lists every Root CA installed on your machine. Search for eDellRoot. It should look like this.
Dell XPS 15 with the eDellRoot certificate installed pic.twitter.com/X5UFZKFoU7
— Adam (@_xpn_) November 23, 2015
If it’s there, you’ve got the dodgy certificate installed. To delete it, right click the certificate, and click Delete.
You can also find out if you are effected with a single line of Powershell code.
Test your Dell with #PowerShell: if(ls cert: -re|?{$_.Thumbprint -eq"98A04E4163357790C4A79E6D713FF0AF51FE6927"}){"eDellRoot found"}
— Mathias Jessen (@IISResetMe) November 23, 2015
Given the size of Dell, the vast number of affected machines, and the propensity for businesses to use Dell machines, I guarantee there’ll be some major fallout from this episode. Apologies will be issued from higher-up, and people will lose their jobs. Tech-savvy consumers will think twice about ever buying a Dell laptop ever again. But what about you?
Were you affected? Will you buy a Dell ever again? Tell me about it in the comments below.
Photo Credits: Dell Keyboard (David Precious)



 Assassin's Creed Syndicate Guide On Flower Locations
Assassin's Creed Syndicate Guide On Flower Locations Where The Game Industry Fails Actors: An Interview With Amanda Strawn
Where The Game Industry Fails Actors: An Interview With Amanda Strawn How to Stream or Broadcast Gameplay videos on PS4 using Twitch
How to Stream or Broadcast Gameplay videos on PS4 using Twitch The Witcher 3 Guide: How to Find Places of Power in the Skellige Isles
The Witcher 3 Guide: How to Find Places of Power in the Skellige Isles How To Spend GTA V PC Pre-order Bonus ($1M Online, $500K Story): Buy 200K Apartment With 10 Car Garage & More
How To Spend GTA V PC Pre-order Bonus ($1M Online, $500K Story): Buy 200K Apartment With 10 Car Garage & More