

Our online lives are consistently at risk of hackers. Even our medical records are greatly sought-after. But it might get worse. A software engineer has recently warned that you should expect your Internet history, specifically any adult sites you’ve visited, to be leaked.
San-Francisco-based Brett Thomas posted on his blog:
“If you are watching/viewing porn online in 2015, even in Incognito mode, you should expect that at some point your porn viewing history will be publicly released and attached to your name.”
If this is the case, it would actually be an even greater concern than a stranger linking your name to adult material. Thomas uses porn as an example because it’s more sensational than leaking the details of which coloring sites you frequent.
Could your Internet history be an open book for hackers? And what can you do about it?

Last year, a number of nude photos were leaked online, labelled ‘Celebgate,’ including images of Jennifer Lawrence, Kirsten Dunst, and Kate Upton. The media attention it brought even led to an ill-advised marketing stunt in which supposedly-compromising pictures of Emma Watson would be part of an upcoming leak.
It turned out to be utter nonsense, but it nonetheless generated press and shows how a group of hackers could potentially gain leverage over individuals if they did obtain NSFW material.
I’m not a celebrity, you might figure, so I wouldn’t be a worthwhile target for hackers.
Sadly, that’s simply not true. The fact that adult content can be used to take advantage of anyone is the prime reason horrible practises like sextortion are on the increase. Social media, too, is a considerable target, as seen during the so-called Snappening, with an alleged 200,000 Snapchat accounts leaked onto 4chan. Why? Sometimes for extortion, and at other times, just as a sign of power, to show people they can.
Look at the damage caused by the Ashley Madison leak! It’s very serious – with real world consequences.
After noting these high-profile privacy issues, Brett Thomas’ claim seems more than reasonable. As he theorises:
“At any time, somebody could post a website that allows you to search anybody by email or Facebook username and view their porn browsing history. All that’s needed are two nominal data breaches and an enterprising teenager that wants to create havoc.”
It’s best you observe standard procedures to secure your privacy anyway, including limiting the amount of data you give to Facebook; using Incognito or Private Browsing; or switching to a search engine that doesn’t track you, like DuckDuckGo.
But these won’t stop a hacker determined to link your IP address to porn or otherwise NSFW websites.
If you’re concerned about such a leak, there are a few things you can do to limit the damage.
If you’re after anonymous Internet surfing, your best bet is a Virtual Private Network (VPN). Enabled by encryption and tunnelling (that is, scrambled information delivered across a secure link between two interfaces), many of us already use VPNs at work, perhaps on remote sites to access the company Intranet.
There are plenty of reasons to use a VPN, but particularly that it will skip your online searches being logged by Google, Bing, or whoever.
It’s not unhackable, but without an encryption key, anyone trying to decipher your private information will find it much harder. Your IP address is also hidden, so it’ll be tougher to link that data to you specifically. Here’s a handy list of the best VPNs, listed in specific groups: premium (ie. paid-for), free, and torrent-friendly.
This is a whole different level of encryption. Just like the aforementioned VPN system, Tor bundles allow the exchange of information between public keys, but it further directs that data through onion routing.
Using proxy servers, the information can be traced back to an IP address, but the result will be the proxy server, not your actual home. Still, that can lead back to you relatively simply. However, onion routing muddies the water even further, directing data packets through several nodes and encrypting at every point.
It’s not perfect. Only the endpoint can decrypt the information sent, so hackers could only get jumbled-up gibberish at the intersecting junction. But that does mean that an endpoint is its weakest spot; the National Security Agency (NSA), for example, is targeting Tor browsers especially.
It does remain your best option for privacy.
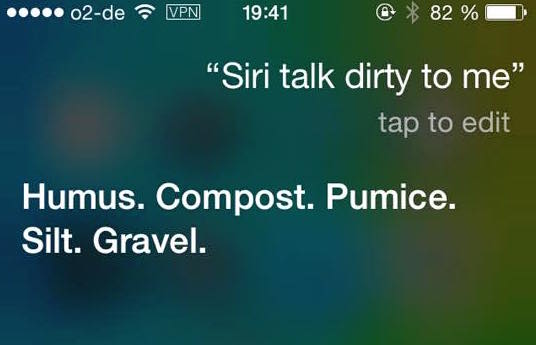
Voice assistants on phones are no doubt handy, but they also guzzle up data. Whether we give Siri, Cortana, and Google Now too much information is an entirely different argument, but that data is nonetheless collected. As all three know your location (with Cortana and Google Now even capable of distinguishing your home from your work), depending on your settings, such information could be used by hackers to link you to a specific area, making you and your searches more identifiable.
Collected statistics are then sent securely to Microsoft, Apple, and Google – but it could still be victim of an interceptor. So what can you do?
On iOS, you’ll need to toggle your settings: Settings > Privacy. Here, you can not only change your Location Services but also Diagnostics & Usage from Automatically Send to Don’t Send; this limits the data you send to Apple.
Similarly, you can go on Customize Google Now and turn off background data (although this does stop downloads and synchs).
Cortana can be changed using the Notebook. You’ll want to deselect Cortana can give you suggestions, ideas, reminders, alerts, and more, which is at the top of the Settings section on Windows 10. Cortana’s suggestions come from the information it stores in the cloud (a system even the NSA think is safest), but you can tamper with it by going on Manage what Cortana knows about me in the cloud. From there, you can clear personal info.
Or if you’ve got Microsoft Edge, open that app and then: More actions > Settings > View Advanced Settings and turn off Have Cortana assist me in Project Spartan.
Beware: limiting what voice assistants can do really can affect your device’s usefulness, but if this really is a big concern to you, it’s worth doing.

Google knows a lot about you. If you’ve got one of their accounts, it keeps a large amount of information about you, notably your location, details of your Gmail, and your search history. Google says it’s solely used to “improve your user experience and the overall quality of [their] services.”
Essentially, it’s for personalization, including advertising, but all that private info in one centralized place? Not good.
You can discover what they know by visiting Google Dashboard,but there’s not a great deal you can do – apart from disable their personalized search results, and using a different search engine. Stay signed out of your Google account while scouting the Internet too.
Incognito mode won’t stop such info being collected, but browsing through a VPN or Tor software should do.
The problem, of course, is that we don’t know what form a potential hack might take, so it’s difficult to protect yourself. If Brett Thomas is right, a lot of people will be sweating.
Your best bet right now is to practise best privacy protocols.
Would this be the ultimate result of our ongoing privacy violations? What further tips do you have?
Image Credits: Kate Upton by Peter Ko; People Network Via Shutterstock; Google Logo by Robert Scoble.



 Mystery House in Japan Walkthrough
Mystery House in Japan Walkthrough The Witcher 3 Guide: How to Get Superior Potions, Bombs, Oils, and More
The Witcher 3 Guide: How to Get Superior Potions, Bombs, Oils, and More How to Customize Your PS Vitas Home Screen
How to Customize Your PS Vitas Home Screen Minecraft Xbox 360: How to Guide
Minecraft Xbox 360: How to Guide Ouya’s “Free the Games” Promotion Incites Dubious Kickstarter Behavior
Ouya’s “Free the Games” Promotion Incites Dubious Kickstarter Behavior