

Data security and privacy is increasingly difficult to understand. How can we be truly sure that the messages we’re sending don’t fall into the wrong hands, and the photos we upload don’t get misused?
To understand data security loopholes and how we can avoid them, MakeUseOf spoke with Shaun Murphy. Murphy is a former government security consultant and the founder of Sndr, a free messaging and file-sharing app that he claims solve the most common problems with encrypted data and online security.

We often hear of how the government is reading our emails and how all our text communication is not secure. The common solution offered is to encrypt your emails. These solutions work as a layer on top of email, in the form of cryptographic plugins. However, it’s usually not a practical solution.
“It puts the onus on your recipients to also have the same plugin, exchange some shared secret code/key to read your messages,” Murphy says. “These layers usually add so much friction in communicating with everyone you already know, that people end up abandoning it altogether.”

Cryptography, however, is hard to develop; it’s hard to convince people to use it; and very hard for companies to give up the ability to data mine all of your messages and data, he adds.
“No one or no entity should have access to private citizen’s messages and data that were not clearly intended for public consumption. And for that we need wide adoption of cryptography services between sender and recipients on everything—email, messaging, social media, file sharing. It’s just too risky to leave this stuff unprotected on servers spread out across the world. That’s where Sndr comes in, by putting all of that in one place.”
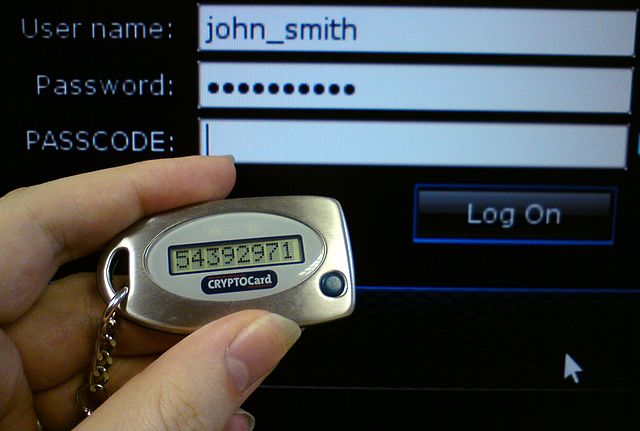
Murphy recommends two-factor authentication (also called 2FA or or 2-step verification) as the best way to first secure your inbox against intruders. 2FA is a double-step security protocol, available for most prominent web services. After you input your password, the service sends a second code, usually via SMS, to ensure it’s really you.
“This is a very strong authentication mechanism since it requires something you know (password) and something you have (mobile device)—typically, someone with malicious intent will not have access to both,” Murphy says. “Authentication is essential to starting to secure your communication. Remember, if someone gets into your email, they can reset ALL other accounts you have via the “reset my password” links on social media and most other websites… scary stuff!”
Given how powerful Gmail or Outlook or other web-based email clients are now, you probably don’t have an offline client like Outlook Express or Thunderbird. But that’s a mistake, according to Murphy. There are some benefits to using an offline email client like Thunderbird instead of accessing Gmail or Outlook from your browser.
“Your keystrokes won’t be captured (as some social media giant was caught doing recently) as you type your message,” he says. “You have time to review your messages and content for any sensitive information before it is submitted to some connected service. And you can take your time to make sure you connect to a safe network.”
Murphy especially recommends using offline emails clients when you travel. When you are not using your home or office’s Wi-Fi network, you cannot be sure how secure it is. “I do use offline clients when I’m travelling just for the simple reason that most Wi-Fi access points are not safe even if you use many layers to try to protect it,” Murphy says.

XKCD’s comic nails the security secret to passwords, Murphy says. The longer and more complex you make it, the harder it is for a computer algorithm to crack it. So he has two golden rules for passwords:
Complexity can be achieved by special characters, capitalized letters, numbers, etc, Murphy says, offering an example of a really strong password:
Ye8ufrUbruq@n=se
“Well that violates Rule #1: I have to remember that somehow. Forget it, I’ll just write it down or stick in a password remembering program… and that’s not so great for security,” he says. “What if we had a really long password but made it a bit more memorable?” For example:
TodayIsGoing2BeTheBestDayEver!
“The key here is I can remember that, it’s a long passphrase and it is very complex and, to some standards, more secure than the first one just because of the number of characters.”

Emails are often used to transmit important files, from tax return information to sensitive photos. Since we’ve already established the security flaws in email, you need to be doubly sure about these documents. So first put them into an encrypted, locked format and then email them, Murphy says.
After doing one (or both) of those options, you can freely send that file without much worry.
This approach still requires you to send that password to the other person. To be safe, Murphy recommends calling them and saying the password out loud; don’t write it down anywhere. And use the principles of the 30-character password trick to make it memorable and secure.
While our smartphones are slowly replacing our PCs, you can’t treat them as the same type of device when it comes to security practices. The risks are different, and so you need to approach the problem differently. Here’s how Murphy differentiates the risks:
Risks for PCs: A PC is generally set up to allow programs to do whatever they please with the exception of a few hot items (act as a network server, access system or other user files, etc.) Today’s threats on PCs include ransomware—a program that encrypts all of the files you need and forces you to pay them some money to unlock them but the biggie is the silent stuff. Some software programs sit on your computer, crawl the network for juicy stuff and silently transmit those files overseas.

Risks for Phones: A phone’s security issues are generally more restricted than a PC because phones aren’t set up to let programs do whatever they want. However, there are other problems. Phones typically know where you are by the cell phone tower it is connected to, any nearby Wi-Fi, and if you have your GPS module turned on. Downloaded apps may have way too many permissions and might be capturing too much information about you (like accessing your contact list and uploading all of them to a server somewhere).
Murphy’s Tip: Encrypt your phone. On Android you have to explicitly do this in the phone’s settings. The latest iPhones ship this way when you have a password. Here’s how to do it.

Also, the actual technology that makes a cell phone communicate with cell towers is generally a black box that the security community doesn’t have much visibility into the inner workings. Is it capable of remotely controlling your phone, turning it on or activating its camera?
Murphy’s Tip: Use a passphrase for login. A simple 4-digit pin isn’t enough, a 6-digit pin is good, a passphrase is best. And pattern locks are out of the question.
Fingerprint scanners are getting better but they are not a good replacement for passwords. Fingerprints and other biometrics are better suited to replace a username than a password since a password should be something you know. With that said, fingerprint scanners to unlock phones are better than nothing.
Finally, the size of a phone makes it more likely to be stolen. And since it has all your accounts logged in, the thief simply has to reset passwords to lock you out.
Murphy’s Tip: Turn on remote device management. For Apple users, there’s Find My iPhone and for Androids, use the Device Manager. This will let you remotely wipe sensitive data from your device if it is stolen.?
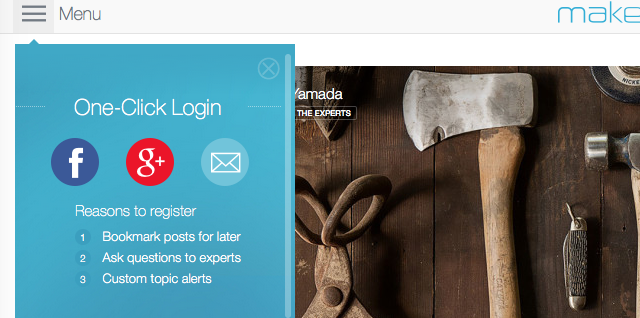
Several sites ask you to sign in using your social accounts. Should you do it?
“It really depends and how much access the site requests for your information,” Murphy says. “If the site simply wants you to authenticate so you can leave comments, try their services, etc. and they request your identity, that’s probably okay.”
“If they ask for all sorts of permission—post to your network ,send messages on your behalf, access your contacts? Watch out!”
At the end of all this, you’re probably wondering which of the many popular services you can use and still be assured of your security. Is Gmail safe? Should you be storing your data on Dropbox? What about security-focussed services?
Murphy doesn’t recommend any current cloud app. The popular, convenient and simple ones lack true privacy and security, he says, while the ones that offer true privacy and security are complex to use and have too much of the aforementioned friction.
So what are Murphy’s recommendations?

For email: “Email is sort of a lost cause. Even if you have the most secure provider, your recipients will always be the weak link.”
For cloud storage: “The best is a server that you control, can lock down at the filesystem level, and ensure each file is encrypted with a unique key per file.”
For office suites: “You can still purchase offline office tools or use open source options. Real-time collaboration takes a hit but some secure/open sourced solutions are starting arrive for that functionality.”
For photos: “I go old school with this, connect to a device in my house, transfer pictures from my device to a long term storage drive (not flash, the data will not survive multiple years without being plugged in) and have an automated program encrypt and upload this information to a server I control. It’s not convenient, but it’s secure, not only from prying eyes but from services that go belly up in a few months, year.”
Got any doubts about your data security? Maybe you have questions about how Sndr can help solve those issues? Fire your questions in the comments, we’ll ask Shaun to weigh in!




 Rain (PSN Game) Walkthrough
Rain (PSN Game) Walkthrough How to earn more Crossy Road PC Coins faster, Tips Guide
How to earn more Crossy Road PC Coins faster, Tips Guide How to do Destiny Farming for Maximum Reputation, Tips and Tricks for PlayStation and Xbox
How to do Destiny Farming for Maximum Reputation, Tips and Tricks for PlayStation and Xbox XCOM vs. XCOM Enemy Unknown: Nerdrage Disaster
XCOM vs. XCOM Enemy Unknown: Nerdrage Disaster Six Misconceptions About Gamers and Gaming
Six Misconceptions About Gamers and Gaming